In my previous blogpost I demonstrated a basic enrollment of Passwordless authentication
into Azure AD with a FIDO2 Security Key.
Generally speaking, common use cases for FIDO2 certified hardware keys are as follows:
- Strong Authentication
- Securing Privileged Accounts
- Passwordless Authentication
- Shared Devices
- Personal Security (Cloud Storage, Password Managers, Social Accounts)
In this post I will focus on provisioning Temporary Access Pass to end users for them being able to add a FIDO2 Security Key as Authentication Method for themselves in Azure AD.
FIDO2 Security Key can then be used as strong authentication during Windows Autopilot enrollment and is an alternative when mobile devices isn’t an option as MFA method.
Finally I will demonstrate that from there, the end user can either:
- Provision their credentials into Windows Hello for Business (Security Key as MFA method)
- Use FIDO2 Security Key as Sign-In method into Windows (recommended for a shared device)
Part 1. Temporary Access Pass and FIDO2 Security Key Enrollment
To provision a Temporary Access Pass we need to be able to enable the method and target it to a group (or All Users). This is done in Azure Active Directory \ Security \ Authentication Methods
We should note here that the properties and lifetime of the TAP-method can be adjusted as seen on the screenshots below. In my example I configured it like this:


When the method is enabled and targeted, we can add a TAP to a user graphically in the Azure Portal.
Select the user and Authentication Methods then select Add authentication method.

Select Temporary Access Method (preview) as method, then select Add.

The details are then provided for us and the next step should be to send the information to the end user for registration.

We can also provision TAP with Powershell instead of the GUI. See the example below:
Part 2. Use TAP as Sign-in for enabling strong authentication method (FIDO2 Security Key)
The end user navigates to My Security Info and then enters their email.

Instead of being prompted for their password, the end user will be prompted to enter their Temporary Access Pass instead.

Sign-In successful!

Let’s add Security Key as authentication method. Select Add method, choose Security key and click Add.

Select the type of the security key-

Insert the Security Key into the PC, then select Next.

Verify with OK, twice.


Time to create a PIN for this security key.

Verify with OK.

Finish the setup by touching the security key.

Finally, the end user needs to name the security key.

All Set!


Part 3. FIDO2 Security Key Sign-In, Autopilot Enrollment and Windows Hello for Business Provisioning
The end user has a new Windows 10 device which is in Windows Autopilot and the end user has access to the newly enrolled Security Key. Computer is powered on and the end user goes through the initial OOBE-steps until the end user arrives at the Sign-in.

Insert the security key into the PC. Here, the end user selects Sign in with security key. The end user then enters their security key PIN. And confirms their presence by touching the security key.

After successful Sign-In, Autopilot Enrollment is initiated.

Scenario A – Personal Device (WHfB Enrollment)
If the user or device is targeted with a Windows Hello for Business-policy (from MEM) the WHfB Enrollment will initiate usually at next Sign-in. This is the most suitable authentication method if the device is a personal device. When the Autopilot provisioning is done, the end user is prompted for setting up Windows Hello for Business.
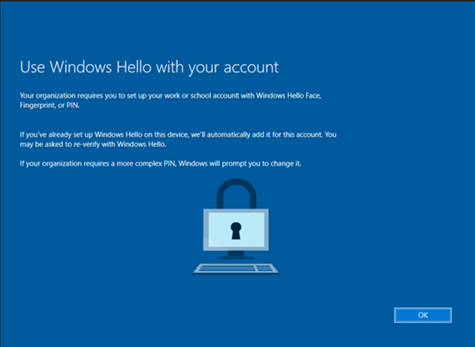
Windows Hello for Business enrollment is initiated and since the PC has fingerprint sensor that method is presented first.
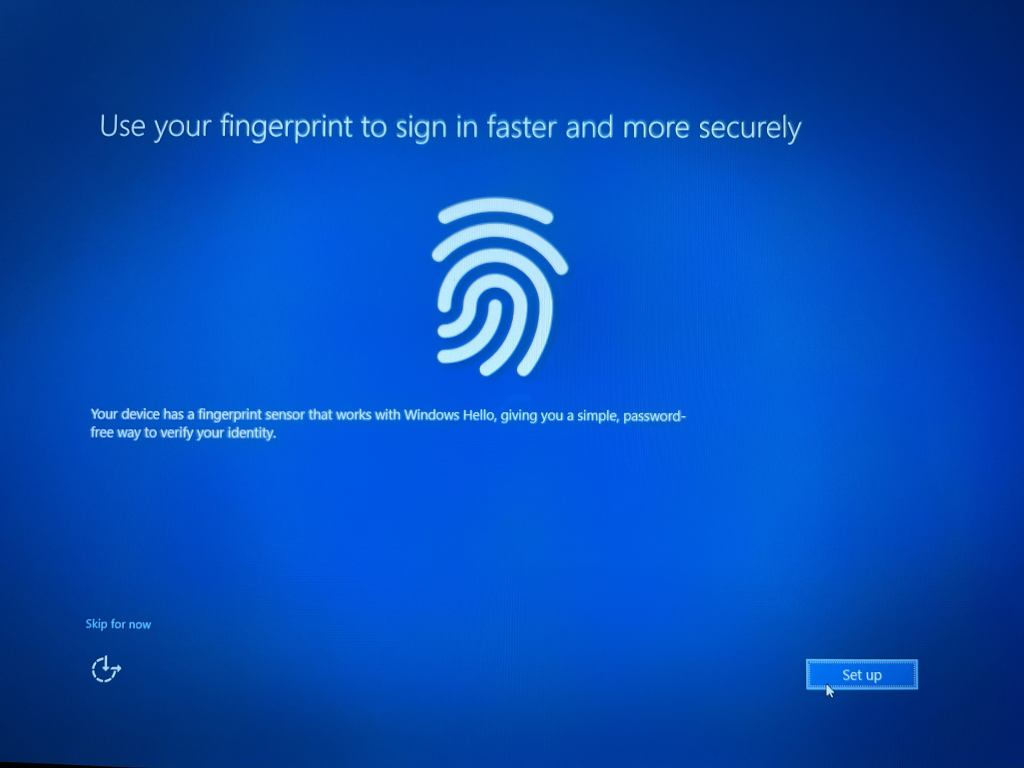
The end user then sets up the PIN for WHfB, encrypted and safely stored locally in the PCs TPM chip.

Success! Enrollment and Sign-In without using a password!

Scenario B – Shared Device (FIDO2 Windows Sign-in)
When the Autopilot provisioning is done (and Windows Hello for Business-policy is not targeted at the user), the end user can now Sign in into Windows with their Security Key instead of a password. This is the ideal authentication method when the device is shared or when mobile devices isn’t an option as MFA method.

The end user selects Sign-in options, then selects FIDO security key and inserts the key into the PC.
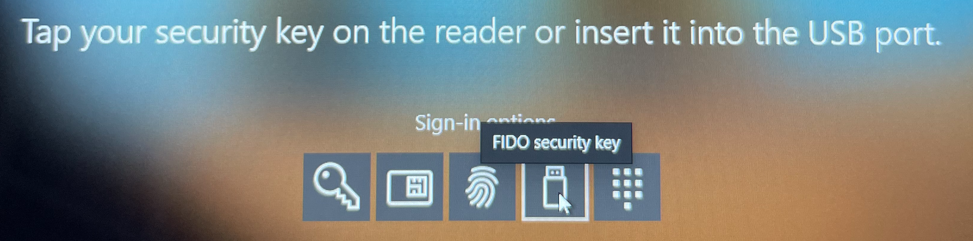
Enter PIN, then touch the security key.

Success! Enrollment and Sign-In without using a password!

For Passwordless Sign-In into Windows, see these Specific requirements for Azure AD Joined and Hybrid Azure AD Joined devices. If the device is using Windows 10 version 1903 or higher the end users themselves can adjust their security key biometric, PIN or reset their security key.
Windows Settings > Accounts > Security Key
As noted on Known Issues, administrator provisioning and de-provisioning of security keys is not yet available. However, we can at least as administrators remove the authentication method In Azure AD.




















